Imagine the internet as a bustling café, where everyone’s chit-chatting away, sharing stories, secrets, and sometimes, their mother’s secret cookie recipe. Now imagine if anyone—yes, even that shifty-eyed guy in the corner—could eavesdrop on your conversation. Creepy, right? That’s exactly what happens when you share unencrypted data online. But fear not, dear reader, for the superhero of our tale, is here—Encryption!
Understanding Encryption
Remember those secret languages you made up as a kid, where ‘fudge’ meant ‘homework’ and ‘pickle’ was your annoying little brother? Encryption is kind of like that, but a gazillion times more complex. In the simplest terms, encryption is a method of converting plain text into an unreadable format, called ciphertext, to prevent unauthorized access.

Think of encryption as a magical decoder ring. What looks like gibberish to everyone else makes perfect sense when viewed through the ring. It transforms your sensitive information into a mess of characters that would give even the most tenacious codebreaker a run for their money.
The Role of Encryption in Online Privacy
So how does this digital decoder ring protect your online privacy? Well, imagine you’re sending a postcard to a friend. Without encryption, your message is open for the world to see. With encryption, however, your message is sealed in an envelope, invisible to prying eyes.

When you send encrypted data over the internet, you’re essentially putting your private information in a high-security vault. Only those with the correct key can unlock it. This ensures that your personal details, financial transactions, and secret cookie recipes remain confidential.
Types of Encryption
Now that we’ve covered the basics, let’s dive into the types of encryption. Think of them as different kinds of invisible ink. Some are perfect for passing notes in class, while others are ideal for sending top-secret messages to spies.
Symmetric Encryption
First up is Symmetric Encryption, or as I like to call it, the “Classic Code”. This method uses the same key to encrypt and decrypt data.
Imagine this scenario: You’ve got a secret – a juicy one – and you need to share it with your best friend. But, you’re in a crowded room. You can’t just blurt it out, can you? No, you need a method. A secret language, perhaps? That’s essentially what symmetric encryption is all about.
In the simplest terms, symmetric encryption is a type of encryption where only one key (a secret key) is used to both encrypt and decrypt electronic data. Think of it like a lock and key. You lock your secret message with a key, send it across the crowded room (or the internet), and your friend uses the same key to unlock it. Voila! Secret shared, and no one else is the wiser.
How Does Symmetric Encryption Work? An Example.
Let’s get a bit more technical, shall we? But don’t worry, I’ll keep it as painless as possible. Remember our secret message? Let’s say it’s “Buy Dogecoin.” Now, you want to encrypt it using a secret key, let’s say “1234”. The encryption process jumbles up your message using this key, turning “Buy Dogecoin” into something like “Qx9Zv7Dogecoin” (Disclaimer: This is a gross oversimplification, but you get the idea).

Image Source: Khan Academy
Now, this encrypted message is sent to your friend. They take the key “1234”, apply it to the message, and, like magic, it turns back into “Buy Dogecoin”! That’s symmetric encryption in action.
Pros and Cons: Is Symmetric Encryption Right for Me?
Symmetric encryption has its strengths and weaknesses, just like anything else. On the plus side, it’s fast and efficient, making it great for large amounts of data. On the downside, if someone gets their hands on your secret key, they can decrypt your messages and even pretend to be you. So, while symmetric encryption is a powerful tool, it’s important to handle those keys with care.
Asymmetric Encryption
Next, we have Asymmetric Encryption, the “Double Agent”. This method uses two keys—a public one to encrypt data and a private one to decrypt it. It’s like sending a locked box and keeping the key to yourself. Anyone can put something in the box using a public hole, but only you can unlock it to see what’s inside.
Imagine you’re passing notes in class (come on, we’ve all done it). You want to make sure that if your note gets intercepted by the ever-watchful eyes of Ms. Smith, she won’t be able to read it. So, you and your buddy come up with a code. That’s encryption: turning readable information into gobbledygook that only certain people can understand.
Now, imagine you’re passing notes with someone you’ve never met. You don’t have a secret code because, well, you’ve never met. Enter Asymmetric Encryption! Also known as Public Key Encryption, this is a way to scramble your note so only the intended recipient can read it, even if you’ve never swapped secret codes before.
Here’s how it works.
Everyone has two keys: a public key, which is like your mailbox, and a private key, which is like the key to your diary. When someone wants to send you a secret message, they lock it with your public key. Once it’s locked, not even the sender can unlock it again. Only your private key can do that.
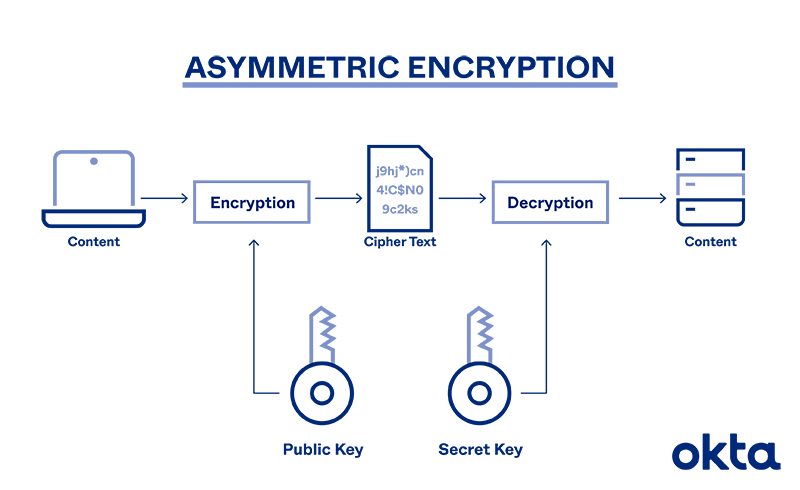
Image Source: Okta
And voila! You’ve got yourself a securely encrypted message. It’s like magic but without the rabbits and top hats.
So why is this important? Well, this is the backbone of secure communication on the internet. Every time you see that little padlock in your browser bar, asymmetric encryption is hard at work, protecting your information from prying eyes.
Doesn’t it feel good to know that there’s something out there, tirelessly working to keep your secrets safe? I mean, who knew that math could be your best friend?
Alright, that’s enough geeking out for one day. Just remember, the next time you’re passing notes in class, thank the genius minds behind Asymmetric Encryption. And maybe consider paying more attention in class. Just a thought.
End-to-End Encryption
Lastly, there’s End-to-End Encryption, the “Ultimate Secret Keeper”. This method ensures that only the communicating users can read the messages.
Have you ever wondered how your private messages stay so…well, private? Let’s say, for instance, you’ve just sent a steamy text to your significant other or maybe a top-secret cookie recipe to your grandma. How does that information get from point A (you) to point B (them) without falling into the wrong hands? The answer, my friend, is in a magical little thing called end-to-end encryption.
Imagine you’re sending a love letter (yes, in this day and age!) but instead of sending it directly, you put it in a box, lock it up with a key only your beloved has, and then send it off. Even if someone intercepts the box, they can’t read the letter because they don’t have the key. End-to-end encryption works similarly. It scrambles your data into a code that only the recipient can decode. Now that’s what I call love!
How Does This Magical System Work?
Here’s the fun part. When you send a message, it’s encrypted using a unique key (think of this as the lock on the box). This key is stored only on your device and the recipient’s device. Since the key is never shared with anyone else, not even your service provider, no one but you and the person you’re communicating with can unlock and read your messages.

Let’s Get Practical
Image Source: Preveil
Let’s dive into an example. WhatsApp, our beloved messenger that promises privacy, uses end-to-end encryption. When you send a message, it’s encrypted on your device before it’s sent out. It travels through the world wide web in its encrypted form until it reaches your friend’s device, where it’s decrypted for them to read. Even if someone manages to intercept the message while it’s in transit (like some evil postman), all they’ll see is a bunch of gibberish.
Real-life Examples of Encryption
Encryption isn’t just for tech nerds or secret agents. It’s part of our everyday life. Ever noticed that little padlock symbol next to the URL when you’re online shopping? That’s encryption at work, protecting your credit card details from cyber thieves.
And those private chats on your favorite messaging app? Yep, end-to-end encryption is making sure your gossip stays between you and your friends. But what happens when encryption fails? Remember the big news about data breaches where millions of users’ data was compromised? That’s what a world without effective encryption looks like.
How to Ensure Your Data is Encrypted
So, you’re itching to become a master of encryption? Excellent! Here’s your quick-start guide to becoming a privacy pro.
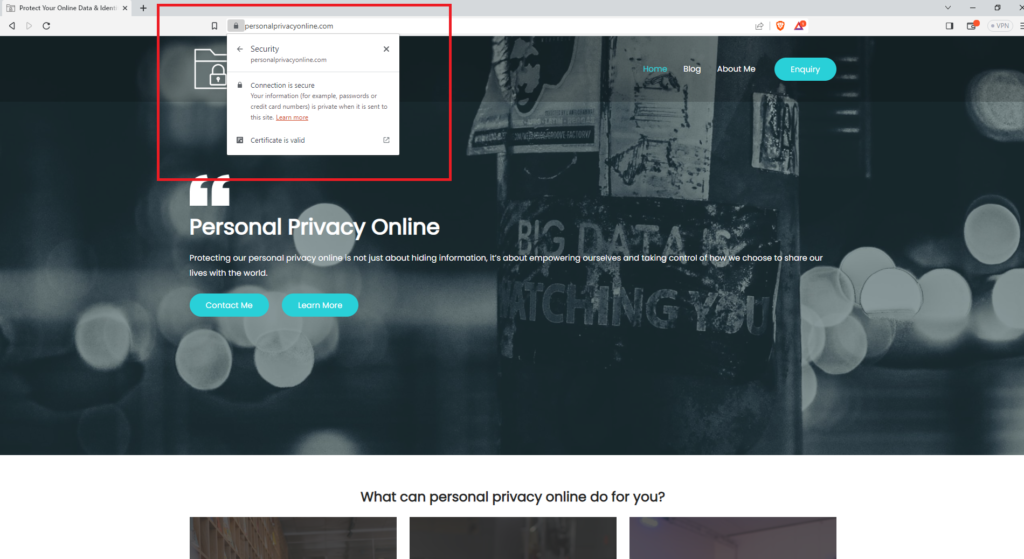
First off, check for that tiny padlock in your browser’s address bar when visiting a website. That’s the SSL certificate, and it means your connection to the site is encrypted. No padlock? Proceed with caution, my friend.
Next up, look for apps and services that offer end-to-end encryption. This ensures only you and the intended recipient can read what’s sent. It’s like having a private conversation in a public place, but you’re both using a secret language only you understand.
Finally, consider using a VPN or Virtual Private Network. A VPN is like a secure tunnel through which your data travels, safe from prying eyes. It’s the digital equivalent of Harry Potter’s invisibility cloak for your data.
Key Takeaways
- Encryption is your online privacy’s best friend. It’s the secret language that keeps your data safe from prying eyes.
- There are different types of encryption: Symmetric (the classic code), Asymmetric (the double agent), and End-to-End (the ultimate secret keeper). Each has its own strengths and uses.
- SSL certificates (the tiny padlock in your browser) mean that a site’s connection is encrypted. No padlock could mean potential danger.
- Apps and services with end-to-end encryption ensure that only you and the intended recipient can read what’s sent. It’s like whispering secrets in a crowded room.
- Using a VPN is like giving your data Harry Potter’s invisibility cloak. It provides a secure tunnel for your data to travel through, away from snooping eyes.
- Data breaches and compromised user information are the consequences of failed or absent encryption.
- Encryption protects everything from your private messages to your credit card details during online shopping.
- Understanding how encryption works is the first step to enhancing your online privacy.
- Sharing unencrypted data online is like shouting your secrets in a crowded café – anyone can hear them.
- Knowledge is power, or in this case, the key to encryption and better online privacy.
Best Tools for Privacy
And now, let’s talk about our top picks for tools that can help enhance your online privacy:
- Brave Browser: This isn’t just a browser; it’s a privacy fortress. Brave goes beyond just encryption to block third-party ads and trackers that compromise your privacy. It’s like having a bouncer for your browsing experience, keeping unwanted guests out.
- Proton VPN: Proton VPN is like the James Bond of VPNs – suave, sophisticated, and absolutely secure. They offer top-notch security features and a strict no-logs policy.
- Bitwarden Password Manager: Remembering a gazillion passwords can be tough, but reusing them is a big no-no for online security. Enter Bitwarden, your trusty password manager. It securely stores all your passwords and auto-fills them when needed. It’s like a digital vault for your passwords; yes, it uses encryption too!
- Signal Messenger: You know how we talked about end-to-end encryption? Well, Signal Messenger is a champion of that. This messaging app is so secure, even Edward Snowden recommends it! With Signal, you can chat away knowing your conversations are for your eyes only. It’s like having a super-secret clubhouse right in your pocket.
That’s a wrap!
So there you have it! Ten key takeaways on encryption and three rock-solid tools to boost your online privacy. Now, go forth and conquer the digital world with your newly acquired knowledge!
With the digital world buzzing louder each day, understanding the role of encryption in protecting your online privacy is more crucial than ever. It’s not just about keeping your secrets secret; it’s about ensuring that your personal space isn’t violated in the bustling café of the internet.
From recognizing SSL certificates to using services like Brave Browser, Proton VPN, Signal, and Bitwarden Password Manager, you’re now equipped with the knowledge and tools to secure your online presence. Remember, in this vast digital landscape, encryption is your invisible shield, your secret language, and most importantly, your key to privacy.
So here’s to safer browsing, more secure transactions, and the peace of mind that comes with knowing you’re protected. After all, in the world of online privacy, knowledge truly is the key (and yes, we’re still loving that pun!).
Did you enjoy this journey through the world of encryption? Don’t keep it to yourself! Share it with your friends, drop a comment with your thoughts, or subscribe for more tech insights delivered with a dash of wit. Remember, when it comes to online privacy, we’re all in this together!

