Do you know why you should be using Multi-Factor Authentication? A solid security plan is essential to maintaining your personal privacy online. Security plans come in many different shapes and sizes. Some are simple and easy to maintain and some are complex and in-depth.
On that note, keep in mind that adding more security to your systems usually means you’re adding in a process that will slow you down. A good example of this is adding a lock to your front door.
If your door doesn’t have a lock then you can come and go as quickly as you like. Still, the moment you add that extra security measure, in order to ensure that it works properly you now have to slow down and make sure to enable the security measure(locking your door in this case.)

Clearly, locking the door will slow you down, but even as much as it slows you down, we often find that it’s worth the sacrifice in speed and efficiency to have the peace of mind that the lock brings. Keep in mind that a lock itself doesn’t provide an immense amount of protection from anyone, but it will slow down and deter possible intruders. Additionally, when combined with other measures like a security system, a second lock, and a great dane the protection yielded should be exponential.
The Keys to the Kingdom

Passwords and Multi-Factor Authentication
Most individuals rely on a single password and email for all their online activity. This practice is risky. If a hacker gains access to this combination, they essentially have the ‘Keys to the Kingdom’.
The Risk of Single Password Use
With one password and email, a hacker can control all accounts associated with them. They can test this combination on numerous popular sites, potentially compromising critical aspects of your life, such as your bank account or social media profiles.
The Power of Multi-Factor Authentication
In such scenarios, multi-factor authentication acts as an extra layer of security, akin to a second deadbolt on your front door. It could be the only thing protecting your bank account from a hacker.
The Importance of Multi-Factor Authentication
This is why multi-factor authentication is crucial in your online security plan. It’s an essential tool to safeguard against potential breaches.
What is Multi-Factor Authentication? What is 2FA?
Multi-factor authentication has a few different names and acronyms. Here are a few of the names it goes by:
- Multi-factor authentication (MFA)
- Two-factor authentication (2fa)
- 2 step verification
Understanding Multi-Factor Authentication
Multi-factor authentication involves using multiple identifiers to confirm your identity. This could include a combination of passwords, fingerprints, facial recognition, authenticator apps, or text-based authentication (SMS). It requires two or more ways to verify who you are.
Application of Multi-Factor Authentication
This authentication method is common when applying for loans or passports. You’ll usually need to provide emails addressed to your home, social security cards, and government IDs. These organizations must confirm your identity beyond doubt.
The Importance of Multi-Factor Authentication
If someone falsely applies for a loan, they could potentially take the money and disappear. Similarly, unauthorized access to a passport could lead to severe damage. Therefore, access to sensitive information is secured by multiple layers of authentication.
You’re Password Sucks (Mine Did Too)
You cannot have a discussion about MFA without discussing passwords because when it comes to online security a password is often the first and only line of defense. Unfortunately, it’s also one of the weakest forms of authentication.
Simple passwords are easy to remember
I still remember creating my first password(which I won’t share with you here). My brother and I had been talking about a concept and a simple word stuck in my head. When I went to create a password that day for my first email account I used that simple 6 letter word and away
I went.
We make simple passwords because they are simple to remember. People will often use common words, names of children, or streets where they live. Some people will even keep a list of their passwords right on their desks. Whatever we can do to help us remember. Unfortunately, this only contributes to the weakness of our passwords.

Password reuse is the norm
The password I created for myself was very simple, so I knew it would be easy for me to remember, but I couldn’t have guessed how much I would reuse that password over the years. I imagine I used that password for over 50 separate accounts in the first year and hundreds in not
thousands of times more after that.
My password didn’t stay exactly the same of course. Whenever the system asked me for a more complicated password like a capital letter, a symbol, or numbers I’d just happily append these onto my current password. Eventually, it looked something like this:
Password123!
Granted, it wasn’t exactly this bad, but to a hacker cracking my password would have been like taking vegetables from a baby. Password reuse like this is incredibly common. The problem is the more you use the password the more likely it is to get revealed in a data breach. While there are many companies that do a great job protecting your data there are many more that don’t and once a password is compromised and linked to an email account it’s all over.
Complex passwords are hard to remember
Have you ever tried to create a complex password? Have you seen an example of a really good password? Let me show you:
SNjnRH81#GTigZ8Xy1gwy!
This is a very secure password that likely won’t be cracked until the dawn of quantum encryption. The problem though is apparent. Complex passwords are hard and sometimes impossible to remember and even if you could remember a single complex password, you’d still have the problem of password reuse.
The moral of the story is that passwords, while sometimes effective, are like a doorknob lock. Nice to have in place, but much more effective when used in combination with a deadbolt.
How can 2FA protect your accounts?
Thus far we’ve talked a lot about multi-factor authentication, but I’d like to dive specifically into 2FA. 2 Factor Authentication is a type of multi-factor authentication where we introduce a second factor aside from our password into the authentication process. Here’s how it works:
1) Go to a site where you’ve enabled 2FA
2) Enter your username and password as usual
3) Then you’ll see a prompt to enter your authentication key
4) Your authentication key can come via SMS, Authenticator App, or a device such as a Yubikey.
5) If you have entered the correct authentication key then you’ll be allowed to proceed.
Clearly, as I mentioned before this process can slow down the speed at which you can access your account. The additional process isn’t always quick. To help aid in this site owners can set different measures for their implementation of 2FA such as only requiring authentication every 30 days or whenever the user is logging in from an unrecognized device. Measures like this can help keep security high and measures stringent where needed, but also ease restrictions on sites with inherently less sensitive data.
This method protects your account by acting as a second lock on your account. If your password is compromised, then the user would still have to have access to your phone, phone number, or device in order to gain full access to your account. Because of the inherent weakness of passwords, this method is essential to protecting your online privacy and security.
Types of 2FA and How They Work
Text-Based 2FA(SMS)

Text-based 2FA is a method of authentication where a secret number is sent directly to your phone. When you’re setting up 2FA you’ll be required to enter your phone number and usually, you’ll receive a verification text to verify your phone number.
Once activated, when you return to the site where you enabled 2FA, and after you enter your login information you’ll be prompted to enter the code which was sent to your phone, thus validating that you are the owner of the account. Check your phone for the text, which is usually a unique 4-6 digit number, and enter it where prompted. Once entered you’ll be able to proceed with logging into the site.
Of the methods being discussed here, it’s important to note, that while valuable, compared to the other methods mentioned this is the weakest form of 2FA, and when possible you should rely more on authenticator applications or a device such as a YubiKey.
There are many factors that go into this, but one of the main ones is that phone numbers can be intercepted or hijacked by tech-savvy hackers. Which could again lead to a compromised account. While unlikely in the case of an average user, this is still something to take into consideration.
Multi-Factor Authentication: Authenticator applications
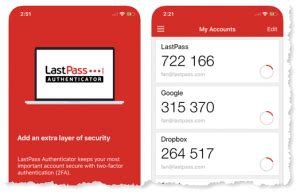
Authenticator applications are applications that live on your phone or device. They work in a similar fashion to SMS Authentication, except they are able to bypass the process of being sent via text. The fact that they aren’t sent over text inherently makes the authenticator application a more secure option.
Authenticator apps work by generating a unique, 6-digit, one-time passcode(OTP) that you can enter into the site to confirm that you are who you say you are. These passwords refresh every 30 seconds which means that even if a hacker or bad actor is able to intercept a code it will be invalid almost immediately after. This forces the user who is logging into an account to actually have the device each time they log in. This means if they don’t have access to your phone, they shouldn’t have access to your account.
Here’s how you set up an authenticator app
First, you have to decide which one you’re going to use and there are quite a few options. Google Authenticator, LastPass Authenticator, Microsoft Authenticator, Authy, FreeOTP Authenticator, and many more all offer their own spins on the authenticator app.
Then, once you’ve decided which one to use, you’ll download and install the application on your phone. Now you’re ready to get started using the application.
From here you’ll log into any app that supports 2FA and head to the settings, security, or privacy area. This is where you’ll usually find settings related to setting up 2FA. During set up the application will require you to scan a barcode with your authenticator app and then you’ll be prompted to enter the next one or two passcodes that the authenticator generates for that site and then you should receive a confirmation that the setup was successful. From there each time you log into that site you should be prompted to enter your 2FA code when accessing that site.
Of the three options listed here, the authenticator app has been my favorite. You can get one for cheap or for free, setup is simple, and they are secure. The SMS option lacks some of the baked-in security of the authentication app, and the Yubikey will stand out more to advanced users as we’ll talk about next.
Don’t lose your phone and definitely don’t lose your backup codes
One important thing to note about using an authentication app is that most of these applications do not support multi-device functionality. This means that your device, backup codes, or system backup are the only means of recovery. So it’s important that when you set up a device and it offers the option to backup your data or to download the recovery codes that you actually do this and(if using the backup codes) that you put them somewhere safe. Preferably an actual safe or some other means of secure storage where you can recover if needed. You never want to be stuck in a situation where you cannot get back into your own accounts so take this aspect seriously!
YubiKey

Exploring YubiKey as a 2FA Method
When deciding on a two-factor authentication (2FA) method, YubiKey is worth considering. It’s a hardware device used for 2FA that plugs into a USB port. To authenticate, simply tap the device when prompted.
Pros of Using YubiKey
The major advantage of YubiKey is its simplicity. Once plugged in, a simple tap authenticates you, eliminating the need to open an app each time. This speeds up the process, making 2FA more convenient. Furthermore, having the YubiKey separate from your phone ensures that any damage or loss of your phone won’t affect your 2FA method.
Cons of Using YubiKey
However, YubiKey has its drawbacks. Being a physical device, it must always be with you and not lost. Its small size can be a disadvantage if you’re prone to misplacing items. You also need to remember to unplug it from your device when not in use, as it could be stolen if left unattended.
Moreover, using YubiKey on multiple devices can be tedious. Imagine plugging and unplugging it every time you want to authenticate on different devices.
Final Thoughts
For those working in high-security environments, YubiKey may be a suitable 2FA method. However, for beginners, an Authenticator app might be a simpler option.
So if you’re still reading, then I’ll assume I’ve convinced you that a 2FA is a necessary part of your security plan. If so then check out part 2 of this series where I’ll cover which 2FA application is best.

Pingback: Brave vs Chrome: The Ultimate Browser Showdown for Safety
Pingback: Privacy Tools: Top 10 Picks for the Savvy Internet User